Hunting for Blue Mockingbird samples
In my recent post about XMRig-based CoinMiners spread by Blue Mockingbird Group based mainly on Case Study by LIFARS I wrote about multi-stage attack performed by this threat actor. However, this case study doesn’t contain lot of IOCs (one reason could be to maintain privacy of the victims), and when I want to analyze these samples, first I have to find them somewhere. In this post I describe my process of searching for these samples using public services and how we can reconstruct the whole attack chain.
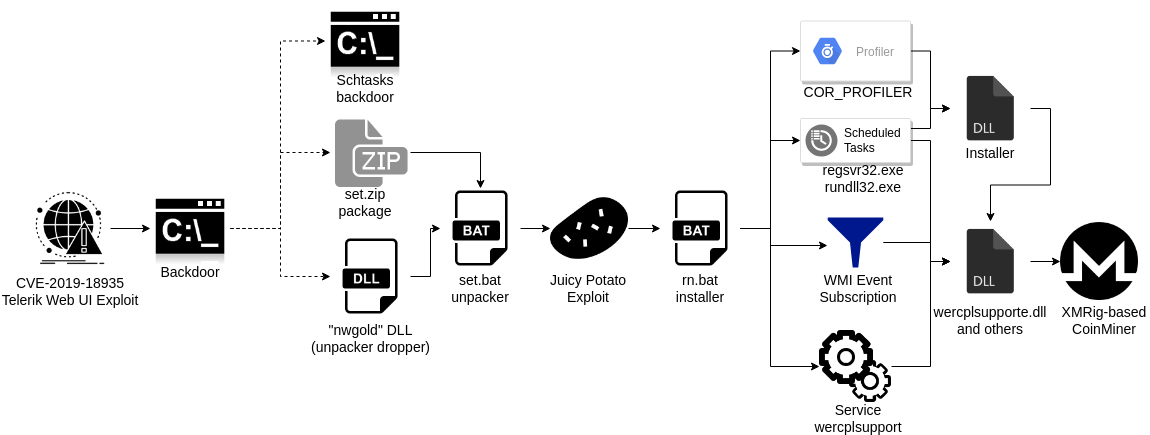
The attack chain includes multiple malware samples, from exploits through backdoors and installers to the coinminers with lot of persistence artifacts. But the question is, how and where can I find and download these samples for my analysis?
Malware Repositories
As a malware analyst I often start with only a some of the indicators or attributes of malware samples such as hashes, filenames, commandline arguments, URLs, IP addresses and ports. These indicators could be retrieved from IDS, SIEM and other security solutions, but malware samples themselves are often not present. They could been already deleted, or even not detected and captured by security solutions. For example, the network monitoring can detect suspicious TCP communication and then I want to find malware associated with it.
Thus, as a part of Incident Response and Threat Hunting process, I often have to use Threat Intelligence methods and find the malware samples elsewhere. A good point to start is searching various online databases such as:
- VirusTotal,
- Hybrid-Analysis,
- Any.Run,
- MalShare,
- URLhaus,
- and others, see for example this list by Lenny Zeltser.
Especially if I already know hash of particular sample but not sample itself, I can try to find the sample in that databases. However, these databases are quite useful also in case, when I have another piece of information instead of hash, for example URL or IP address associated with the malware, filenames, category or I already know malware family, but also it is possible to search by strings embedded in the malware samples.
Some of these databases also offer a possibility to search for related, linked or similar samples, e.g. Virus Total Relations, Community Comments, or special Virus Total Graph feature; Hybrid-Analysis advanced search; Any.Run Context search filter. And, of course, we also always can try a generic search engines such as DuckDuckGo, Google, etc.
Blue Mockingbird Samples
OK, that was a theory, let’s go to do something practical. I already mention Blue Mockingbird group, my recent article and Case Study by LIFARS. But as you may notice, none of them contains any IOC hashes. Instead, they contain multiple keywords, filenames, some generic URLs of coinmining pools, etc.
It is no problem, we just have to find some IOCs on the Internet. For example, Google search for “blue mockingbird malware ioc” returns me the article on SecurityIntelligence.com, which contains reference to the Red Canary Report in first paragraph.
The report by Red Canary contains Indicators of compromise for XMRIG miner DLLs as well as Indicators of compromise for COR_PROFILER DLLs.
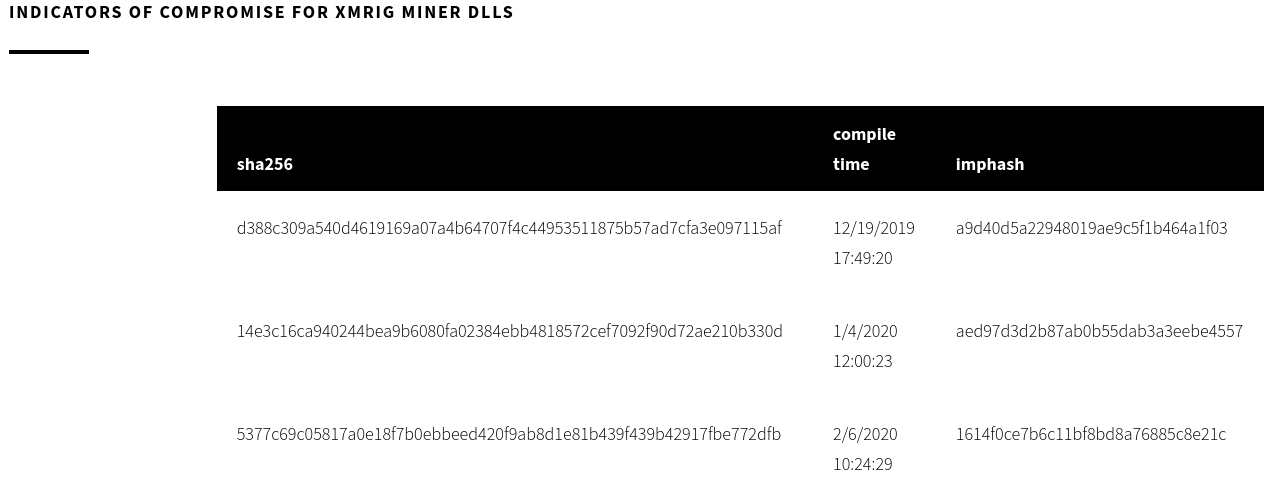
We can use these hashes one by one and search the online malware repositories manually. Or, we can speed up this process and use a clever tool called Munin by Florian Roth. All we need to do is create one file with these hashes and let Munin to do its work.
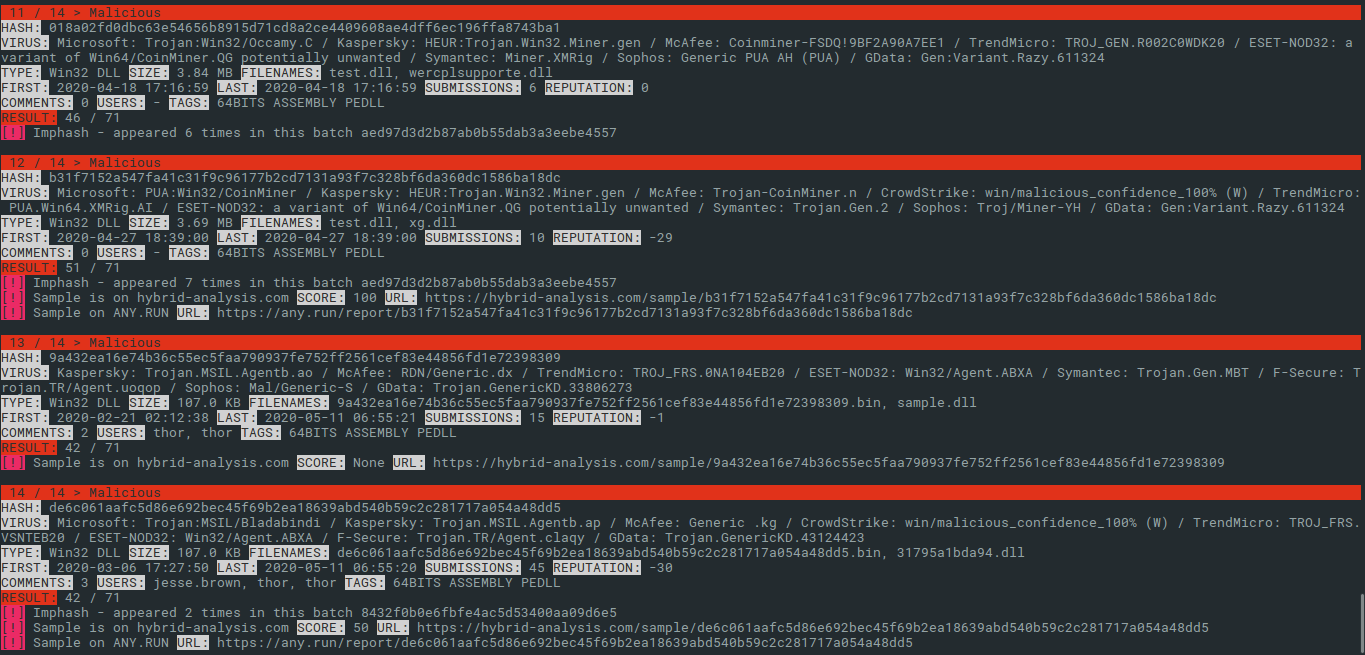
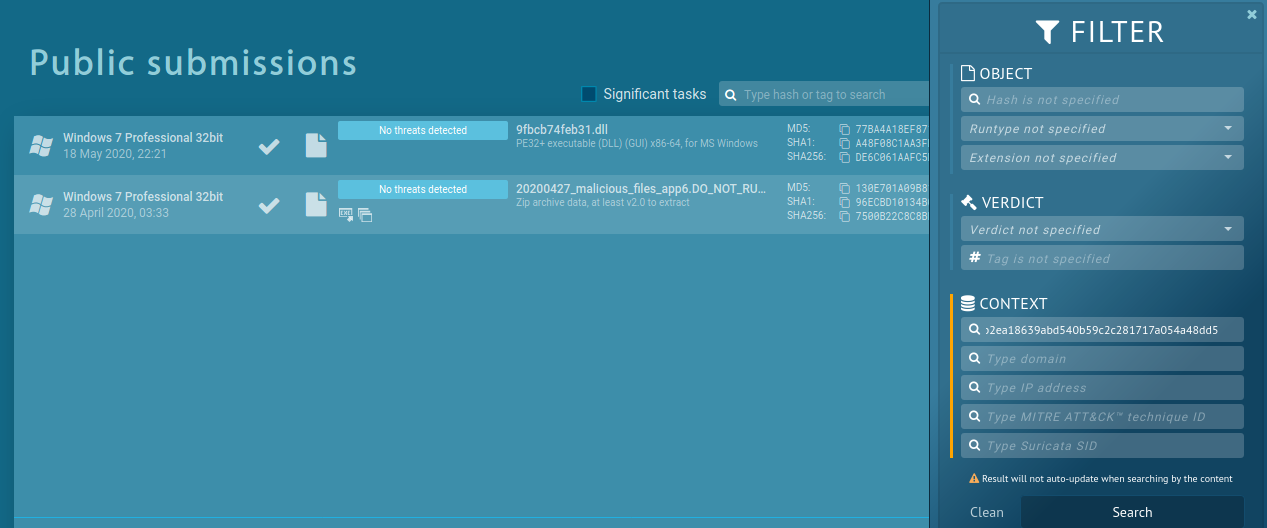
We can see from Munin output that some of these 14 hashes are available on Hybrid-Analysis or on Any.Run. Even with free account on Any.Run, we can download these samples for our analysis. However, we can do more. For example, let’s pick the last hash for COR_PROFILER DLL; de6c061aafc5d86e692bec45f69b2ea18639abd540b59c2c281717a054a48dd5 and search for them on Any.Run. There is only one public submission (on 18th May 2020), without any threat detected.
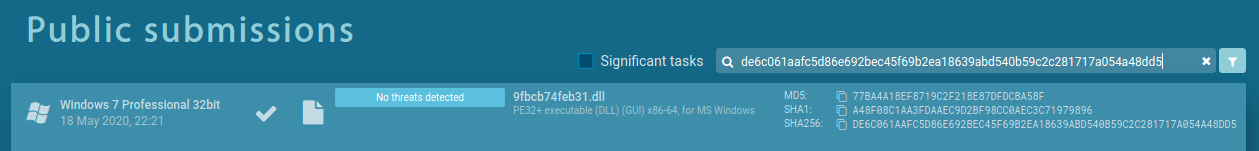
Now, let’s do a “trick”: instead of search and filter by object hash, we can filter public submissions by context, see screenshot below. And now, we will get older submission (on 28th April 2020) of ZIP with potentially malicious files.
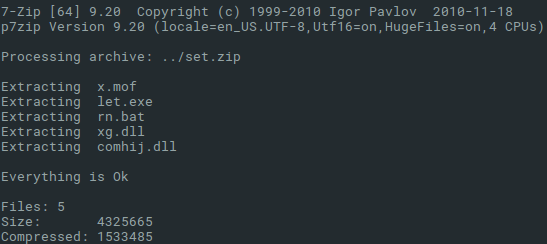
When we review the Any.Run analysis and look inside of the uploaded ZIP file, we find the golden nugget. It contains a couple of DLLs, two .bat and one .mof file. When we look on them carefully, we noticed that all of them were referenced in my previous article. Yes, this is how I get these samples for my public analysis suitable for my personal blog.
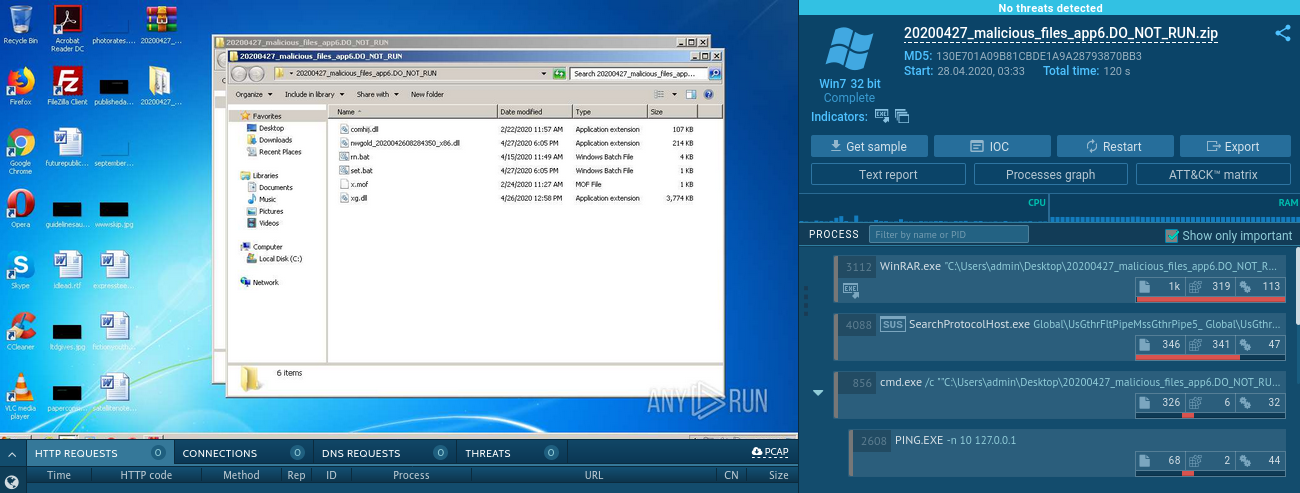
However, when the user ran the set.bat, it complains about unknown program let.exe and it seems that no malicious activity was detected.
Unfortunately, one, maybe two pieces of puzzle are still missing - program let.exe referenced in rn.bat and complete package set.zip. When we find let.exe somewhere, probably we should be able to reconstruct the set.zip archive. Or, better, we can try to find the original set.zip somewhere.
We already tried search capabilities and filters on Any.Run, but because we did not have luck with search by hash we should either use something else such as tags (e.g coinminer, xmrig, …), domains or IP addresses associated with these coinminers. Please note, that nowadays Any.Run doesn’t support filtering by sample object filename as they did before (and it was very useful feature, of course).
On the other hand, there are also other repositories, not only the Any.Run. For example, I mention above that Hybrid-Analysis supports Advanced search, so let’s utilize it and try to search for let.exe or set.zip submissions and in case we find multiple results, we should investigate those from April and May 2o2o.
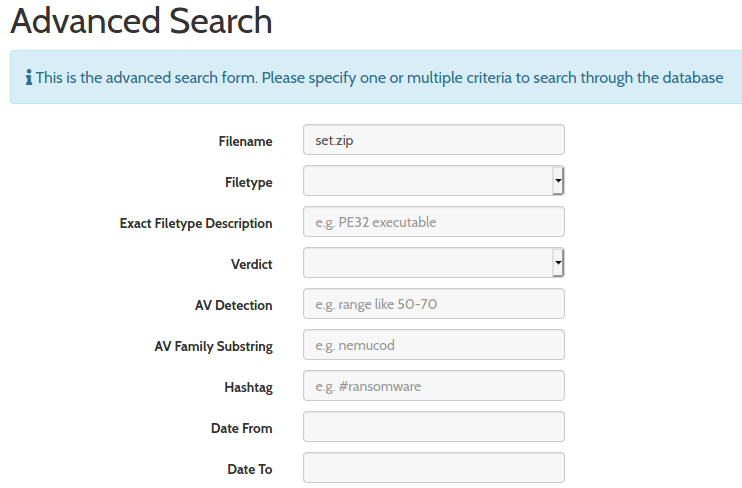
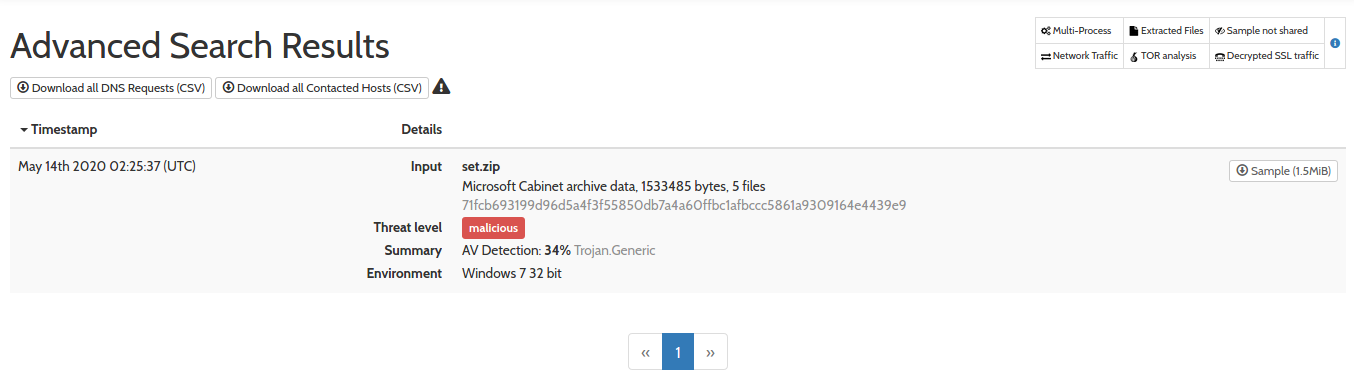
And guess what? We are lucky, there is only one set.zip submission from May 14th 2020, and I have vetted account, so I can download this sample. After examinining its content, I can confirm that this is the set.zip we were looking for.
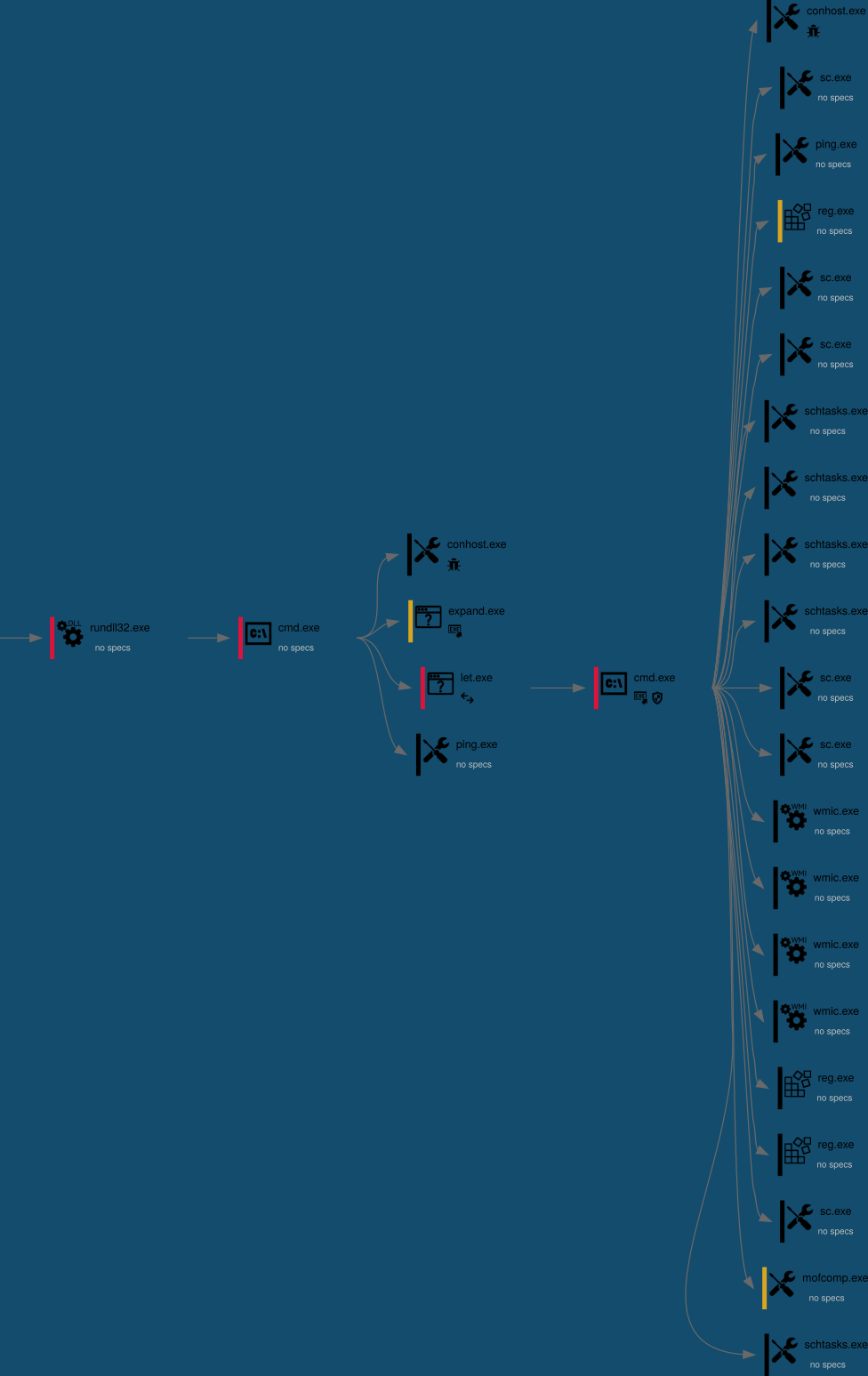
Behavioral analysis Blue Mockingbird Samples
Now it is time to put it all togehter and replicate the previously documented phases of Blue Mockingbird attack chain. We can start with nwgold DLL and set.zip package and we should be able to observe its unpacking, Juicy Potato privilege escalation, installation of CoinMiners and various persistence methods. My tool of choice for this kind of behavioral analysis is Any.Run, because I have to put these nwgold and set.zip files inside of ProgramData folder and run nwgold DLL, thus I need to interact with the sandbox. And moreover, I like the output and analysis capabilities of Any.Run, so this is my #1 choice.
I had only one issue - the most of the DLLs (CoinMiners and DLL instaler - COR_Profiler) are 64-bit, but the basic free account on Any.Run supports only 32-bit machines. So I try to write request to Any.Run support for temporary access to 64-bit environment especially because this article and they gave it to me. So, a big thanks to Any.Run, see the following tweet and enjoy the video from my analysis.
My new blog post about the #BlueMockingbird #XMRig #CoinMiner #malware samples. Where and how to find them, collect them and analyze them using @anyrun_app #ThreatIntel #malwareanalysis #DFIR #cybersechttps://t.co/Q8BfhZF9rmhttps://t.co/O0AeE7Nxfo pic.twitter.com/3UqkJm0QoF
— Ladislav B (@ladislav_b) June 19, 2020
References
- https://lifars.com/knowledge-center/xmrig-based-coinminer-bluemockingbird-group/
- https://securityintelligence.com/news/blue-mockingbird-attempts-to-distribute-monero-miners-to-enterprise-targets/
- https://redcanary.com/blog/blue-mockingbird-cryptominer/
- https://github.com/Neo23x0/munin
- https://app.any.run/tasks/66ab973a-cb28-4cdf-b91b-f747bc188bef/
- https://www.hybrid-analysis.com/sample/71fcb693199d96d5a4f3f55850db7a4a60ffbc1afbccc5861a9309164e4439e9
- https://app.any.run/tasks/318e4886-35da-4d71-8610-fb6b3964d04b/